大纲
十二、安装并配置病毒扫描与垃圾邮件过滤
十三、安装并配置managesieve插件
十四、常见问题分析
说明:我们继续接着上一博文继续往下面说(上一博文:http://www.okserver.cn/article/html/2015/Email_0924/57.html),首先我们来简单回忆一下我们上一篇博文的主要内容,我们说明了mail架构的主要部件,整个mail系统的工作流程,重点对比了,常规mail架构与精简mail架构的区别,重点说明了dovecot的优点,不仅能提供SASL认证,还是提供LDA功能,且效率大大的提高,不会占用太多有内存资源,然后我们具体演示了精简mail架构的配置过程,包括LAMP环境的搭建、Postfix配置、Dovecot配置、Postfixadmin配置、以及Roundcubemail的配置,完整搭建了整个邮件系统,但没有演示反垃圾邮件与邮件杀毒,在这一篇博文中我们重点讲解,反垃圾邮件与邮件杀毒,还有常见问题分析,好了下面我们就来说一说,嘿嘿!
十二、安装并配置病毒扫描与垃圾邮件过滤
1.安装安amavisd-new、clamav及spamassassin
|
1
|
[root@mail ~]# yum install -y amavisd-new clamav clamav-devel clamd spamassassin |
说明,amavisd-new、clamav及spamassassin可从RPMForge软件仓库安装,想想当年我们手动安装perl模块果,几十个模块一个个安装那叫一个苦B啊,嘿嘿,现在好了可以用yum直接安装,那叫一个爽!
2.查看amavisd-new、clamav及spamassassin开机自启动
|
1
2
3
4
5
|
[root@mail ~]# chkconfig --list | grep "amavisd\|clamd\|spamassassin" amavisd 0:off 1:off 2:on 3:on 4:on 5:on 6:off clamd 0:off 1:off 2:on 3:on 4:on 5:on 6:off spamassassin 0:off 1:off 2:off 3:off 4:off 5:off 6:off [root@mail ~]# |
大家可以看到spamassassin是个服务是停止的开机没有启动,是因为amavisd-new直接将spamassassin作为一个模块使用,所以不需要守护进程,自然开机不需要启动,嘿嘿!
3.修改SpamAssassin配置文件
|
1
2
3
4
5
6
7
8
9
|
SpamAssassin作为amavisd-new的模块是需要特别配置,只要安装就行,但是你也可以定制它通过修改[root@mail ~]# vim /etc/mail/spamassassin/local.cf# These values can be overridden by editing ~/.spamassassin/user_prefs.cf # (see spamassassin(1) for details)# These should be safe assumptions and allow for simple visual sifting # without risking lost emails.required_hits 5 report_safe 0 rewrite_header Subject [SPAM] |
我这里只是列出为给大家看一下,有需要的博友自行修改,我这里就不修改了!
4.修改ClamAV配置文件/etc/clamd.conf
说明,ClamAV的设定存放在/etc/clamd.conf内,我们修改/etc/clamd.conf配置文件让ClamAV知道,Amavisd-new将会利用本地的UNIX通讯端与它通信而不是利用tcp端口来与它通信!
|
1
2
3
4
5
|
[root@mail ~]# vim /etc/clamd.conf#利用本地通信LocalSocket /var/run/clamav/clamd.sock#注释掉TCP通信端口#TCPSocket 3310 |
5.修改Amavisd-new配置文件/etc/amavisd.conf
(1).通过去除以下数行的注释来停止检查病毒域垃圾邮件(由于下面数行默认是被注释掉的,因此病毒及垃圾邮件在预设中默认是被启动的)
|
1
2
3
4
|
[root@mail ~]# vim /etc/amavisd.con# @bypass_virus_checks_maps = (1); # controls running of anti-virus code # @bypass_spam_checks_maps = (1); # controls running of anti-spam code # $bypass_decode_parts = 1; # controls running of decoders&dearchivers |
(2).接着可以看到下面几行
|
1
2
3
4
5
6
|
$max_servers = 2; # num of pre-forked children (2..30 is common), -m $daemon_user = "amavis"; # (no default; customary: vscan or amavis), -u $daemon_group = "amavis"; # (no default; customary: vscan or amavis), -g $inet_socket_port = 10024; # listen on this local TCP port(s)# $notify_method = 'smtp:[127.0.0.1]:10025'; # $forward_method = 'smtp:[127.0.0.1]:10025'; # set to undef with milter! |
说明,
$max_servers 设定同步执行的Amavisd-new进程数量,而且必须与/etc/postfix/master.cf内的amavisfeed服务的maxproc中相符合
$daemon_user及$daemon_group应该用来匹配Amavisd-new的用户及群组
$inet_socket_port 定义Amavisd-new将会在哪一个tcp端口接纳来自Postfix的连接
$notify_method及$forward_method定义Amavisd-new把邮件重新注入Postfix的途径
(3).以下是必须修改项
|
1
2
3
4
5
6
|
$mydomain = 'free.com'; #我这里是free.com域 $MYHOME = '/var/amavis'; $helpers_home = "$MYHOME/var"; $lock_file = "$MYHOME/var/amavisd.lock"; $pid_file = "$MYHOME/var/amavisd.pid"; $myhostname = 'mail.free.com'; #我这里是mail.free.com主机 |
(4).下面是SpamAssassin设定来替换预设的SpamAssassin设置
|
1
2
3
4
5
6
7
8
9
10
11
|
$sa_tag_level_deflt = 2.0; # add spam info headers if at, or above that level $sa_tag2_level_deflt = 6.2; # add 'spam detected' headers at that level $sa_kill_level_deflt = 6.9; # triggers spam evasive actions (e.g. blocks mail) $sa_dsn_cutoff_level = 10; # spam level beyond which a DSN is not sent $sa_crediblefrom_dsn_cutoff_level = 18; # likewise, but for a likely valid From # $sa_quarantine_cutoff_level = 25; # spam level beyond which quarantine is off $penpals_bonus_score = 8; # (no effect without a @storage_sql_dsn database) $penpals_threshold_high = $sa_kill_level_deflt; # don't waste time on hi spam $bounce_killer_score = 100; # spam score points to add for joe-jobbed bounces$sa_mail_body_size_limit = 400*1024; # don't waste time on SA if mail is larger $sa_local_tests_only = 0; # only tests which do not require internet access? |
说明,默认不需要修改但你得知道它们和意义,可以方便的帮助我们设置垃圾邮件‘
$sa_tag_level_deflt 指定Amavisd-new由哪一个级别开始写入X-Spam-Flag、X-Spam-Score、X-Spam-Status等垃圾邮件资讯标头,假如你想为所有邮件加入资讯标头,请把此值设为 -999
$sa_tag2_level_deflt 指定由哪一个级别开始在垃圾邮件的标头上标签它们
$sa_kill_level_deflt 指定Amavisd-new由哪一个级别开始拦截和扣留邮件。这个用途很大,因为SpamAssassin在预设情况下不会这样做
$sa_dsn_cutoff_level 指定由哪一个级别开始寄件失败通告不会被发送给寄件人。由于多数垃圾邮件寄件者的地址都是伪造的,不为明显的垃圾邮件发送寄件失败通告是最合理的,要不然你只会加剧反向散寄的问题
$sa_quarantine_cutoff_level 指定哪一个级别开始不必扣留垃圾邮件。这个选项预设是被注释掉的,意思是所有邮件都会被扣留
(5).下面是发送通告的邮件地址(默认是管理员邮箱,接收垃圾邮件通告的邮箱)
|
1
2
3
4
|
$virus_admin = "virusalert\@$mydomain"; # notifications recip. $mailfrom_notify_admin = "virusalert\@$mydomain"; # notifications sender $mailfrom_notify_recip = "virusalert\@$mydomain"; # notifications sender $mailfrom_notify_spamadmin = "spam.police\@$mydomain"; # notifications sender |
修改为,
|
1
2
3
4
|
$virus_admin = "postmaster\@$mydomain"; # notifications recip. $mailfrom_notify_admin = "postmaster\@$mydomain"; # notifications sender $mailfrom_notify_recip = "postmaster\@$mydomain"; # notifications sender $mailfrom_notify_spamadmin = "postmaster\@$mydomain"; # notifications sender |
(6).设置ClamAV的部分
|
1
2
3
4
5
|
# ### http://www.clamav.net/#['ClamAV-clamd', # \&ask_daemon, ["CONTSCAN {}\n", "/var/run/clamav/clamd.sock"], # qr/\bOK$/m, qr/\bFOUND$/m, # qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ], |
修改为,
#去掉相关注释就行
|
1
2
3
4
5
|
# ### http://www.clamav.net/ ['ClamAV-clamd', \&ask_daemon, ["CONTSCAN {}\n", "/var/run/clamav/clamd.sock"], qr/\bOK$/m, qr/\bFOUND$/m, qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ], |
说明,/var/run/clamav/clamd.sock这个设定必须与我们先前在/etc/clamd.conf内输入的LocalSocket /var/run/clamav/clamd.sock设定相一致。
6.修改Postfix配置文件
(1).修改/etc/postfix/master.cf
|
1
2
3
4
5
6
7
8
9
10
11
12
|
[root@mail ~]# vim /etc/postfix/master.cf# ========================================================================== # # service type private unpriv chroot wakeup maxproc command + args # # (yes) (yes) (yes) (never) (100) # # ========================================================================== # # amavisfeed unix - - n - 2 smtp -o smtp_data_done_timeout=1200 -o smtp_send_xforward_command=yes -o smtp_tls_note_starttls_offer=no -o disable_dns_lookups=yes -o max_use=20 |
说明,请注意在maxproc栏内的数值 2 必须要与/etc/amavisd.conf内的$max_servers设定一致。有关各选项的详细解释请参阅Amavisd-new的文档(vim /usr/share/doc/amavisd-new-2.8.0/README.postfix)。然后我们定义一个专用的服务把邮件重新注入Postfix。我们为此在/etc/postfix/master.cf内加入一个在localhost(127.0.0.1)的tcp 10025端口(/etc/amavisd.conf的预设值)上监听的smtp服务:
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
# ========================================================================== # # service type private unpriv chroot wakeup maxproc command + args # # (yes) (yes) (yes) (never) (100) # # ========================================================================== 127.0.0.1:10025 inet n - n - - smtpd -o content_filter= -o smtpd_delay_reject=no -o smtpd_client_restrictions=permit_mynetworks,reject -o smtpd_helo_restrictions= -o smtpd_sender_restrictions= -o smtpd_recipient_restrictions=permit_mynetworks,reject -o smtpd_data_restrictions=reject_unauth_pipelining -o smtpd_end_of_data_restrictions= -o smtpd_restriction_classes= -o mynetworks=127.0.0.0/8 -o smtpd_error_sleep_time=0 -o smtpd_soft_error_limit=1001 -o smtpd_hard_error_limit=1000 -o smtpd_client_connection_count_limit=0 -o smtpd_client_connection_rate_limit=0 -o receive_override_options=no_header_body_checks,no_unknown_recipient_checks,no_milters,no_address_mappings -o local_header_rewrite_clients= -o smtpd_milters= -o local_recipient_maps= |
注意,以上两项首行前面一定不能有空格,否则会出错!!!
(2).修改/etc/postfix/main.cf加入以下设定来启用邮件过滤
|
1
2
3
|
[root@mail ~]# vim /etc/postfix/main.cf#filter mailcontent_filter = amavisfeed:[127.0.0.1]:10024 |
(3).重启postfix服务
|
1
2
3
|
[root@mail ~]# service postfix restart Shutting down postfix: [ OK ] Starting postfix: [ OK ] |
7.启动clamd及amavisd服务:
|
1
2
3
4
5
6
7
8
9
|
[root@mail ~]# service clamd start Starting Clam AntiVirus Daemon: LibClamAV Warning: ************************************************** LibClamAV Warning: *** The virus database is older than 7 days! *** LibClamAV Warning: *** Please update it as soon as possible. *** LibClamAV Warning: ************************************************** [ OK ][root@mail ~]# service amavisd start Starting Mail Virus Scanner (amavisd): [ OK ] [root@mail ~]# |
9.测试
(1).利用telnet测试amavisd这个服务正在127.0.0.1:10024上监听
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
[root@mail ~]# telnet localhost 10024 Trying ::1... telnet: connect to address ::1: Connection refused Trying 127.0.0.1... Connected to localhost. Escape character is '^]'. 220 [127.0.0.1] ESMTP amavisd-new service ready ehlo free.com 250-[127.0.0.1] 250-VRFY 250-PIPELINING 250-SIZE 250-ENHANCEDSTATUSCODES 250-8BITMIME 250-DSN 250 XFORWARD NAME ADDR PORT PROTO HELO IDENT SOURCE quit 221 2.0.0 [127.0.0.1] amavisd-new closing transmission channel Connection closed by foreign host. [root@mail ~]# |
(2).测试Postfix的smtpd正在127.0.0.1:10025上监听
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
[root@mail ~]# telnet localhost 10025 Trying ::1... telnet: connect to address ::1: Connection refused Trying 127.0.0.1... Connected to localhost. Escape character is '^]'. 220 mail.free.com ESMTP Postfix ehlo free.com 250-mail.free.com 250-PIPELINING 250-SIZE 10240000 250-VRFY 250-ETRN 250-AUTH PLAIN LOGIN CRAM-MD5 250-AUTH=PLAIN LOGIN CRAM-MD5 250-ENHANCEDSTATUSCODES 250-8BITMIME 250 DSN quit 221 2.0.0 Bye Connection closed by foreign host. [root@mail ~] |
(3).垃圾邮件的测试
|
1
2
3
4
5
6
7
|
[root@mail ~]# cd /usr/share/doc/spamassassin-3.3.1/ [root@mail spamassassin-3.3.1]# sendmail test@free.com < sample-spam.txt [root@mail spamassassin-3.3.1]# tail -f /var/log/maillog Jul 11 09:15:46 mail postfix/cleanup[17529]: 6AB1E23776: message-id=<GTUBE1.1010101@example.net> Jul 11 09:15:46 mail postfix/qmgr[17492]: 6AB1E23776: from=<root@free.com>, size=1657, nrcpt=1 (queue active) Jul 11 09:15:46 mail amavis[17520]: (17520-01) Passed SPAM {RelayedTaggedInbound,Quarantined}, <root@free.com> -> <test@free.com>, quarantine: spam-rnWvh9AXIRB2.gz, Message-ID: <GTUBE1.1010101@example.net>, mail_id: rnWvh9AXIRB2, Hits: 1005.069, size: 933, queued_as: 6AB1E23776, 2403 ms Jul 11 09:15:46 mail postfix/smtp[17533]: D927923774: to=<test@free.com>, relay=127.0.0.1[127.0.0.1]:10024, delay=2.7, delays=0.21/0.07/0.02/2.4, dsn=2.0.0, status=sent (250 2.0.0 from MTA(smtp:[127.0.0.1]:10025): 250 2.0.0 Ok: queued as 6AB1E23776)\ |
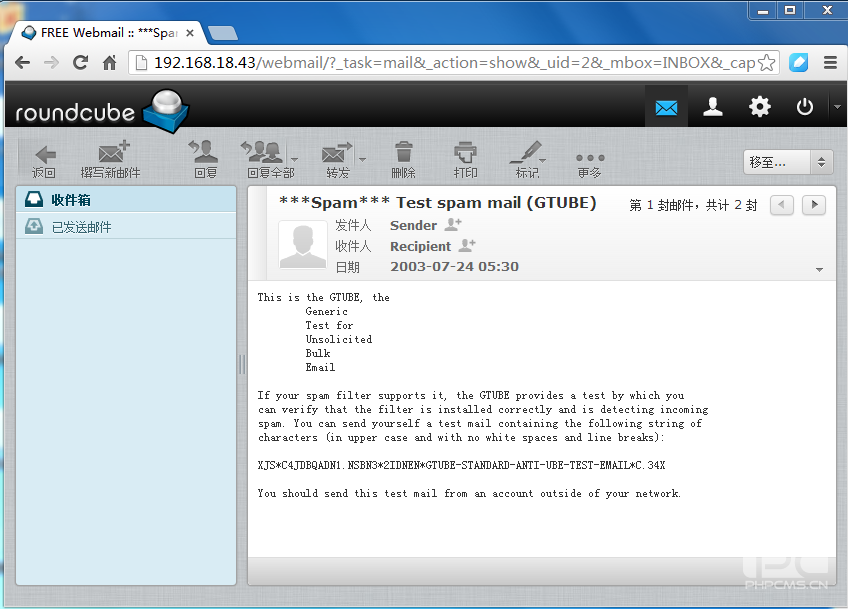
从日志中我们可以看出进行了垃圾邮件过滤,嘿嘿,但效果不明显我们用Webmail测试一下,效果如下,
这就是我们刚才测试的垃圾邮件,嘿嘿!下面我们再发一封测试一下,
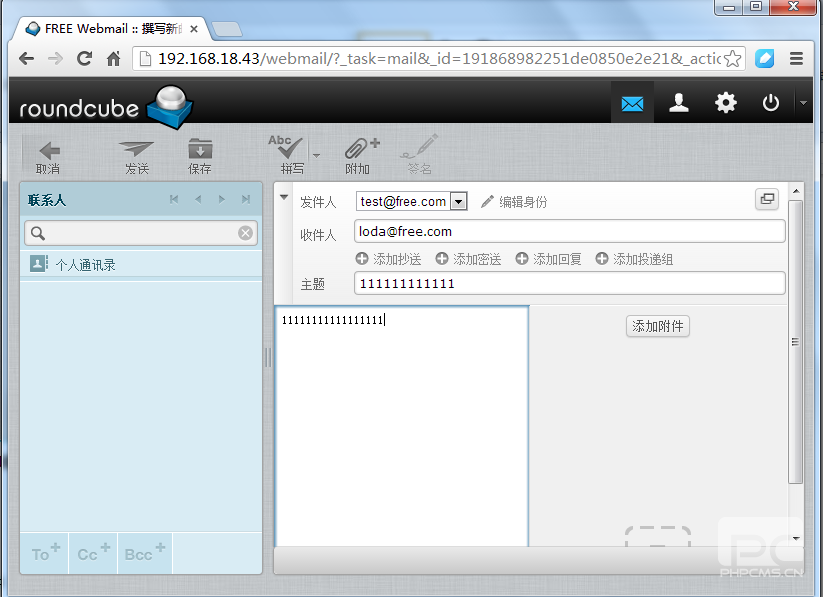
这是我们用test@free.com发给loda@free.com的邮件,我们用loda@free.com接收一下看看效果,
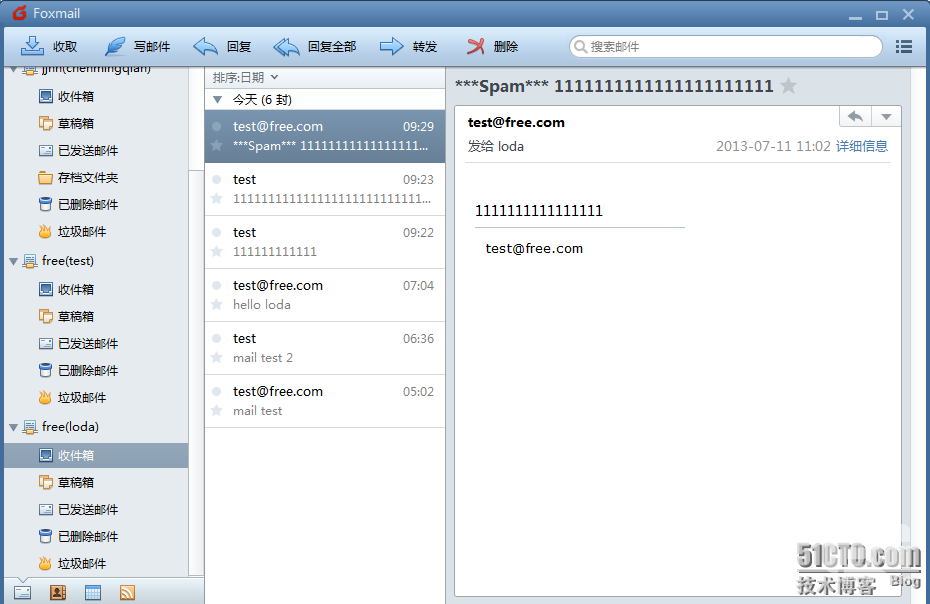
可以看到,当loda接收到这封邮件时,被标记为垃圾邮件!至此所有演示全部完成,嘿嘿,下面我们查看一下所启动的所有服务!
10.查看所有的服务与端口
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
[root@mail spamassassin-3.3.1]# netstat -ntulp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN 1188/mysqld tcp 0 0 0.0.0.0:110 0.0.0.0:* LISTEN 1211/dovecot tcp 0 0 0.0.0.0:143 0.0.0.0:* LISTEN 1211/dovecot tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1050/sshd tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 17489/master tcp 0 0 0.0.0.0:993 0.0.0.0:* LISTEN 1211/dovecot tcp 0 0 0.0.0.0:995 0.0.0.0:* LISTEN 1211/dovecot tcp 0 0 127.0.0.1:10024 0.0.0.0:* LISTEN 17517/amavisd (mast tcp 0 0 127.0.0.1:10025 0.0.0.0:* LISTEN 17489/master tcp 0 0 :::80 :::* LISTEN 16150/httpd tcp 0 0 :::22 :::* LISTEN 1050/sshd tcp 0 0 :::25 :::* LISTEN 17489/master udp 0 0 0.0.0.0:68 0.0.0.0:* 16825/dhclient [root@mail spamassassin-3.3.1]# |
十三、安装并配置managesieve插件
说明,managesieve插件实现邮件过滤和Vacation功能
1.在Doevecot2.0之后的版本,如果需要做邮件过滤的功能需要dovecot-pigeonhole扩展包的支持,
|
1
|
[root@mail ~]# yum install -y dovecot-pigeonhole |
2.配置dovecot配置文件
|
1
2
3
4
|
[root@mail ~]# vim /etc/dovecot/dovecot.confprotocols = imap pop3 sieve[root@mail ~]# vim /etc/dovecot/conf.d/15-lda.confmail_plugins = quota sieve |
3.重新启动dovecot
|
1
2
3
|
[root@mail ~]# service dovecot restart Stopping Dovecot Imap: [ OK ] Starting Dovecot Imap: [ OK ] |
4. 查看Dovecot监听4190端口
|
1
2
3
|
[root@mail ~]# netstat -ntulp | grep 4190 tcp 0 0 0.0.0.0:4190 0.0.0.0:* LISTEN 17998/dovecot [root@mail ~]# |
5.managesieve配置文件修改,将模板复制成config.inc.php,做如下修改
|
1
2
3
4
5
6
7
|
[root@mail ~]# cd /var/www/html/webmail/plugins/managesieve/ [root@mail managesieve]# ls Changelog config.inc.php.dist lib localization managesieve.js managesieve.php package.xml skins tests [root@mail managesieve]# cp config.inc.php.dist config.inc.php [root@mail managesieve]# vim config.inc.php #修改端口为$rcmail_config['managesieve_port'] = 4190; |
6.在主配置文件中使插件生效
|
1
2
|
[root@mail ~]# vim /var/www/html/webmail/config/main.inc.php$rcmail_config['plugins'] = array('managesieve'); |
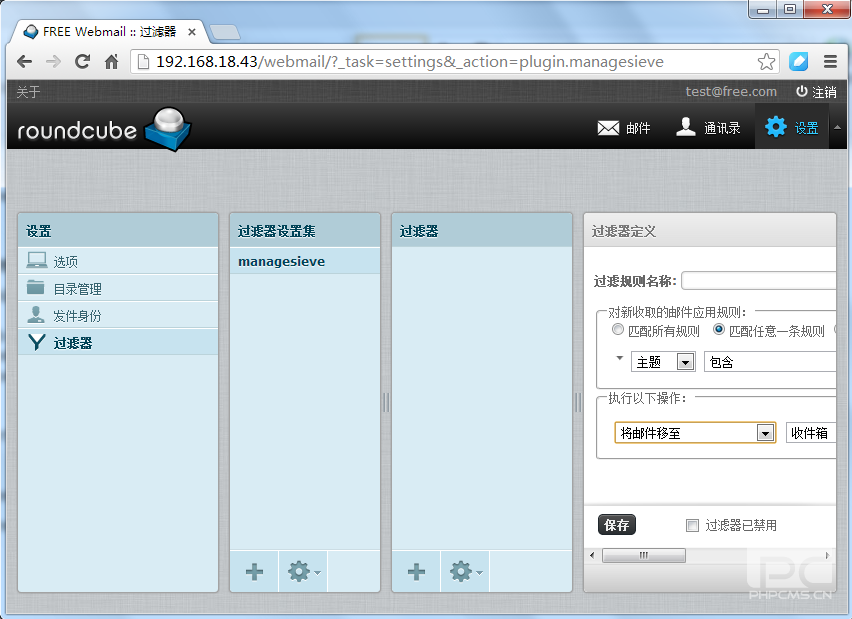
7.效果测试
好了测试成功!Roundcubemail 插件很多,有需要的朋友自行增加就行,^_^……
十四、常见问题分析
说明,说实话这个常见问题分析真不好写,因为我并不知道大家会出什么问题,我这里只说明一下我遇到的一些问题!
1.复制的问题
安装或配置时,很多博友都喜欢复制博客中的内容,会带有一此空格或其它字符,配置文件对这些字符特别的敏感有一点字符可能就支出错,这个特别注意,我自己也遇到过好多次,明明配置都一样为什么你行我不行呢?嘿嘿,这个大家得特别留心!
2.postfix 相关
要查看Postfix的当前主要配置文件的存放路径:postconf -n
系统日志:tail -f /var/log/messages
邮件日志:tail -f /var/log/maillog
3.apache相关
apache相关:tail -f /usr/local/httpd/logs/error_log tail -f /usr/local/httpd/logs/suexec_log
注意,大家可以看到我这里apache运行的用户和组是vmail注意修改
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
[root@mail ~]# ps aux | grep httpd root 16150 0.0 0.0 317840 100 ? Ss 05:59 0:01 /usr/sbin/httpd vmail 16152 0.0 6.5 430908 15428 ? S 05:59 0:04 /usr/sbin/httpd vmail 16153 0.0 7.2 429640 17184 ? S 05:59 0:04 /usr/sbin/httpd vmail 16154 0.0 6.2 428340 14884 ? S 05:59 0:04 /usr/sbin/httpd vmail 16155 0.0 6.6 428624 15672 ? S 05:59 0:04 /usr/sbin/httpd vmail 16156 0.0 5.9 425644 14120 ? S 05:59 0:04 /usr/sbin/httpd vmail 16157 0.0 5.9 425368 14124 ? S 05:59 0:04 /usr/sbin/httpd vmail 16158 0.0 7.2 428068 17224 ? S 05:59 0:04 /usr/sbin/httpd vmail 16159 0.0 4.1 420924 9792 ? S 05:59 0:04 /usr/sbin/httpd vmail 17061 0.0 6.4 427112 15280 ? S 07:04 0:03 /usr/sbin/httpd vmail 17545 0.0 6.2 426612 14804 ? S 09:18 0:02 /usr/sbin/httpd root 18152 0.0 0.3 103236 864 pts/1 S+ 10:02 0:00 grep httpd [root@mail ~]# |
修改方法,
|
1
2
3
|
[root@mail ~]# vim /etc/httpd/conf/httpd.confUser vmail Group vmail |
4.mysql相关
mysql相关: tail -f /usr/local/mysql/data/linux.linux.com.err
5.垃圾邮件相关
测试amavisd: amavisd -d config debug-sa
|
1
2
|
[root@mail ~]# amavisd -d config debug-sa The amavisd daemon is already running, PID: [17517] |
测试spam: spamassassin -D –lint
|
1
|
[root@mail ~]# spamassassin -D --lint |
6.clamd相关
查看 /var/log/clamav/clamd.log
|
1
2
3
4
5
6
7
8
9
10
11
|
[root@mail ~]# tail -f /var/log/clamav/clamd.log Thu Jul 11 09:10:39 2013 -> PDF support enabled. Thu Jul 11 09:10:39 2013 -> HTML support enabled. Thu Jul 11 09:10:39 2013 -> Self checking every 600 seconds. Thu Jul 11 09:22:02 2013 -> No stats for Database check - forcing reload Thu Jul 11 09:22:10 2013 -> Reading databases from /var/clamav Thu Jul 11 09:22:14 2013 -> Database correctly reloaded (1258735 signatures) Thu Jul 11 09:39:24 2013 -> SelfCheck: Database status OK. Thu Jul 11 09:49:24 2013 -> SelfCheck: Database status OK. Thu Jul 11 09:59:24 2013 -> SelfCheck: Database status OK. Thu Jul 11 10:09:24 2013 -> SelfCheck: Database status OK. |
更新病毒库 freshclam
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
[root@mail clamav]# freshclam ClamAV update process started at Thu Jul 11 10:13:58 2013 WARNING: Your ClamAV installation is OUTDATED! WARNING: Local version: 0.97.7 Recommended version: 0.97.8 DON'T PANIC! Read http://www.clamav.net/support/faqmain.cvd is up to date (version: 54, sigs: 1044387, f-level: 60, builder: sven) WARNING: getfile: daily-15077.cdiff not found on remote server (IP: 202.118.1.40) WARNING: getpatch: Can't download daily-15077.cdiff from db.cn.clamav.net WARNING: getfile: daily-15077.cdiff not found on remote server (IP: 200.236.31.1) WARNING: getpatch: Can't download daily-15077.cdiff from db.cn.clamav.net WARNING: getpatch: Can't download daily-15077.cdiff from db.cn.clamav.net WARNING: Incremental update failed, trying to download daily.cvd Downloading daily.cvd [100%] daily.cvd updated (version: 17485, sigs: 1458626, f-level: 63, builder: guitar) Downloading bytecode.cvd [100%] bytecode.cvd updated (version: 214, sigs: 41, f-level: 63, builder: neo) Database updated (2503054 signatures) from db.cn.clamav.net (IP: 202.118.1.40) Clamd successfully notified about the update. [root@mail clamav]# |
查看更新日志
|
1
|
tail -f /var/log/clamav/freshclam.log |
7.dovecot 相关
测试:telnet localhost 110 telnet localhost 143
8.总结
若发现某个服务个有问题或不能收发邮件,最好的方法就是查看相关日志文件,基本都上都是有记录的,只要发现错误,我们便能很快的解决问题